Network teams often manage Wi-Fi, VPN, and admin access as separate silos. Each entry point comes with its own credentials, policies, and monitoring. This fragmentation increases complexity and creates gaps in visibility. As more users connect from remote locations and more devices go unmanaged, enforcing consistent access control becomes nearly impossible.
The Azure Meraki integration brings unity to this fragmented model. By using Azure Active Directory as the central identity authority and Meraki as the access enforcer, organizations can apply the same user policies across VPN, wireless access, and administrative tools. This reduces risk, simplifies IT operations, and improves the user experience.
With identity-first access in place, every authentication request, regardless of where it originates, is evaluated against the same source of truth. In the Azure Meraki model, Azure AD handles the identity logic while Meraki enforces the access outcome.
This means that:
Meraki doesn’t store or manage identities itself. It delegates that role to Azure AD. This separation improves flexibility, reduces overhead, and supports Zero Trust policies by verifying every user and device at the edge.
There are three main access areas in a Meraki environment where Azure AD integration makes an impact:
Each access point relies on Azure AD to validate who is connecting and applies Meraki’s native tools (like VLAN tagging or access policies) to enforce the connection rules. This creates a strong link between user identity and network access behavior.
Choosing the right protocol depends on the type of access you’re securing. Azure Meraki supports both SAML and RADIUS-based authentication through Azure AD. Here’s how to decide:
SAML offers a cleaner, browser-based experience and supports group-based roles for dashboard access. RADIUS is more traditional and supports a wide range of client devices but requires additional setup, including certificate management and group attribute mapping.
Both protocols can be layered with Azure Conditional Access and Duo MFA to strengthen security policies. Meraki doesn’t care which method you use—it simply needs to receive an allow or deny response from your identity service.
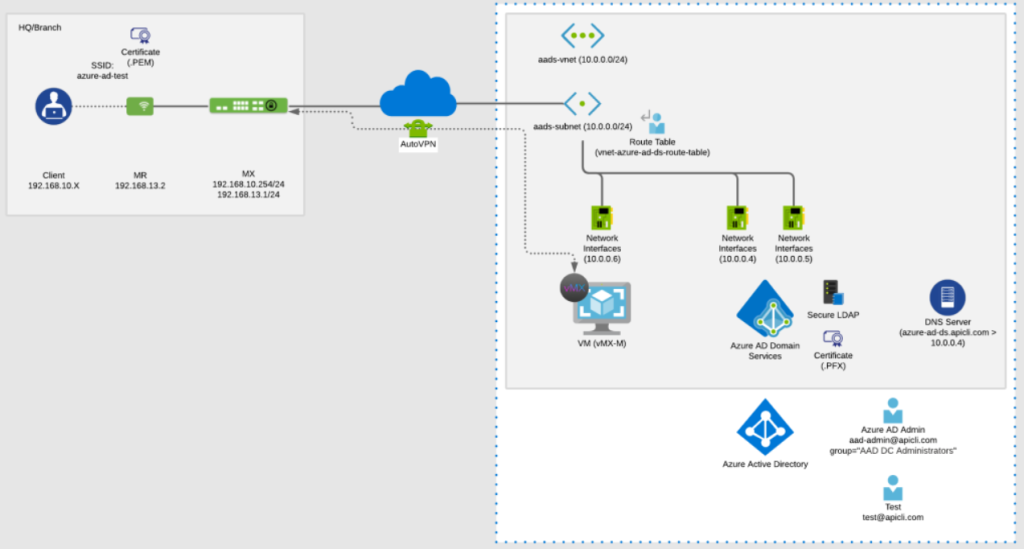
Here’s a basic example of how Wi-Fi access works with Azure Meraki:
The same flow applies to client VPN authentication. In that case, the Meraki MX appliance serves as the VPN gateway, and authentication is handled through a SAML broker that connects back to Azure AD.
This approach ensures consistent access policies across all network surfaces. Every connection is tied to a verified identity and subject to cloud-enforced controls.
The Azure Meraki model supports Zero Trust security by enforcing identity verification at every connection point. Users and devices must prove who they are, meet security posture requirements, and match access policies before entering the network.
With Meraki SSIDs, you can:
With VPN, you can:
This layered access control ensures that users are continuously validated. Access isn’t just granted once but reevaluated with every session, providing ongoing protection against credential abuse or policy violations.
The Meraki Dashboard is a powerful control plane for your entire network. Protecting administrative access is just as critical as securing user connectivity. With Azure Meraki integration, administrators can log in to the Dashboard using their Azure AD accounts through SAML SSO.
Here’s how it works:
This setup ensures that only approved users with verified roles and security posture can administer your Meraki networks. It also allows centralized control of role assignments through Azure AD, reducing risk and streamlining offboarding.
A national retailer with over 50 branch locations recently deployed Azure Meraki integration to secure their wireless, remote access, and admin portals. Before the deployment, each site used pre-shared keys for Wi-Fi, standalone VPN credentials, and locally managed dashboard accounts.
After transitioning to Azure AD:
The results included faster onboarding, reduced helpdesk tickets, and better access control reporting. When employees leave, access to all network surfaces is revoked instantly through Azure AD, without touching the Meraki configuration.
To optimize your Azure Meraki deployment, consider the following tools and settings:
These enhancements increase visibility, reduce misconfigurations, and improve your overall security posture.
Networks that rely on device IPs, MAC addresses, or static VLANs cannot adapt to today’s mobile, hybrid environments. Azure Meraki shifts that model to one built around verified users, trusted devices, and centralized access policies.
By using Azure AD as the identity engine and Meraki as the access fabric, organizations can build networks that are more secure, easier to manage, and better aligned with Zero Trust principles.
Stratus Information Systems helps enterprises design and implement secure, scalable Meraki networks integrated with Azure AD. From Wi-Fi to VPN to dashboard controls, we deliver identity-driven access solutions that work from Day One.
Ready to unify your wireless and identity strategy? Talk to Stratus about Azure Meraki integration today.